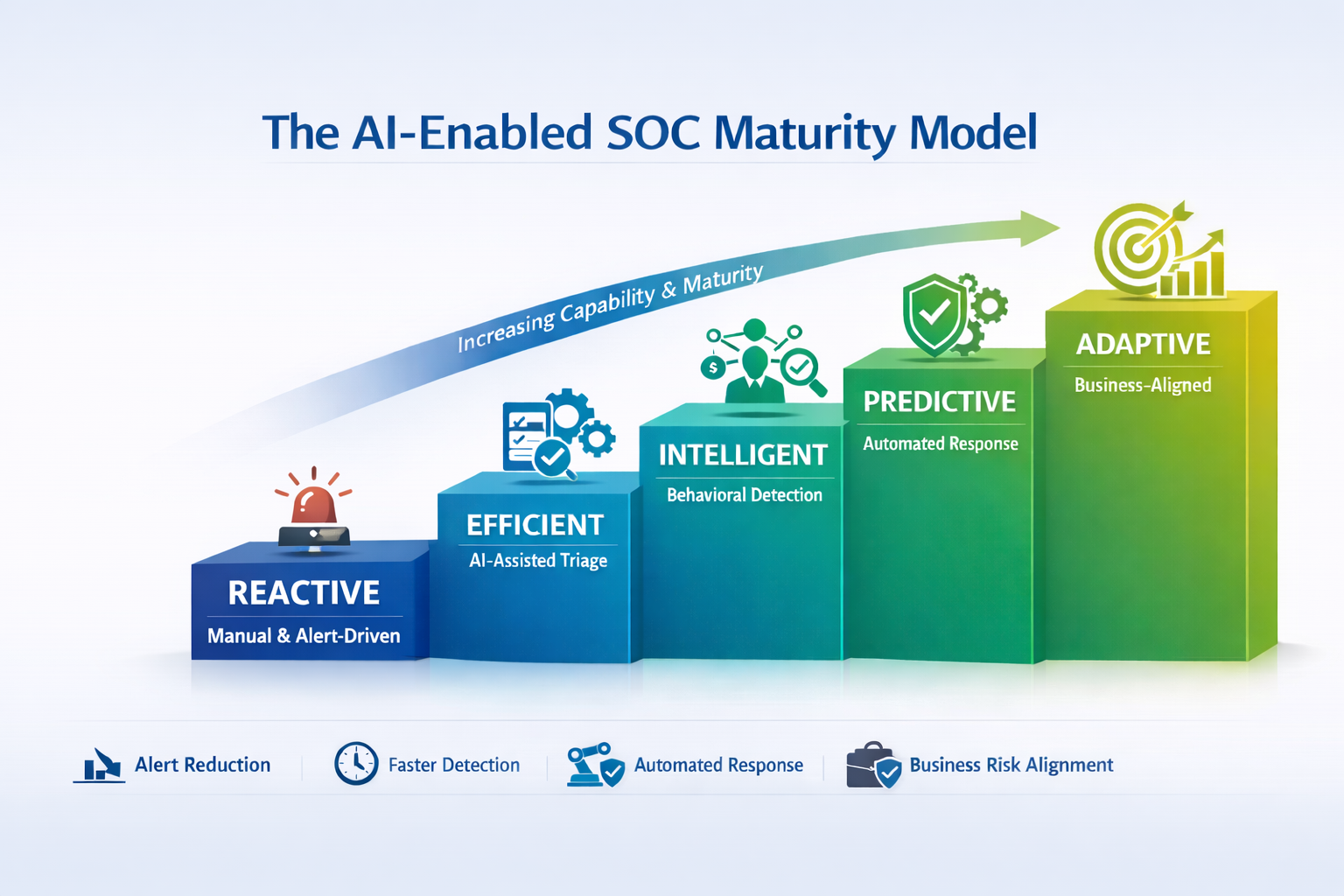
Security Operations Centers do not mature overnight. Most evolve through distinct stages, shaped by alert volume, staffing constraints, and the organization’s ability to translate security data into timely decisions. Artificial intelligence accelerates this evolution by reducing noise, adding behavioral context, and enabling faster, more consistent responses. Rather than viewing AI as a single capability, successful organizations apply it progressively as their SOC processes mature. The following SOC maturity model illustrates how AI capabilities align to each level of operational maturity, moving teams from reactive alert handling to adaptive, business-aligned security operations.
Think of SOC maturity not as “tools deployed,” but as how effectively the SOC turns data into decisions. AI accelerates that journey at every maturity level.
Level 1: Reactive SOC (Manual & Alert-Driven)
Characteristics
-
Primarily rule- and signature-based detections
-
High alert volume, low confidence
-
Manual triage and investigation
-
Reactive incident response
AI Usage
-
None or extremely limited
Operational Reality
-
Analysts overwhelmed by alerts
-
Long Mean Time to Detect (MTTD)
-
Incidents discovered after damage occurs
Typical Metrics
-
False positives: Very high
-
Mean Time to Detection (MTTD): Hours to days
-
Mean Time to Recovery (MTTR): Days
Level 2: Efficient SOC (AI-Assisted Triage)
Characteristics
-
Centralized logging (SIEM)
-
Basic automation and playbooks
-
AI-assisted alert suppression and prioritization
AI Use Cases
-
Alert de-duplication and correlation
-
False-positive reduction
-
Risk-based alert ranking
Business Outcome
-
Analysts spend less time closing noise
-
SOC capacity increases without adding headcount
Typical Metrics
-
Alert volume to analysts ↓ 50–60%
-
Triage time ↓ 30–40%
-
MTTR: Still largely manual
Level 3: Intelligent SOC (Behavior-Driven Detection)
Characteristics
-
Focus shifts from alerts to incidents
-
Behavioral analytics across users, devices, and workloads
-
Context-aware investigations
AI Use Cases
-
User and Entity Behavior Analytics (UEBA)
-
Detection of credential abuse and lateral movement
-
Automated enrichment with threat intelligence
Business Outcome
-
SOC detects attacks that bypass signatures
-
Earlier detection of insider threats and account compromise
Typical Metrics
-
MTTD ↓ 40–70%
-
Detection of “low-and-slow” attacks ↑ significantly
-
Analyst confidence ↑
Level 4: Predictive SOC (Automated & Proactive)
Characteristics
-
High-confidence detections trigger automated containment
-
Human-in-the-loop approval for critical actions
-
SOC operates effectively 24×7
AI Use Cases
-
Automated endpoint isolation
-
Account disablement based on behavioral risk
-
AI-driven incident summaries and recommendations
Business Outcome
-
Threats contained before widespread impact
-
Reduced downtime and breach costs
Typical Metrics
-
MTTR ↓ 50–90%
-
Containment time: Minutes or seconds
-
Blast radius ↓ dramatically
Level 5: Adaptive SOC (Business-Aligned & Learning)
Characteristics
-
SOC aligned directly to business risk
-
Continuous learning and tuning of AI models
-
Metrics tied to outcomes, not alerts
AI Use Cases
-
Predictive risk scoring of assets and users
-
Continuous model tuning based on incident outcomes
-
Executive-level insights and reporting
Business Outcome
-
Security decisions driven by business context
-
SOC becomes a strategic function, not a cost center
Typical Metrics
-
Security incidents with material impact ↓ year over year
-
Analyst burnout ↓
-
Board-level visibility ↑
Key Takeaway
An AI-enabled SOC is not defined by autonomy, but by effectiveness. As organizations move up the maturity curve, AI shifts from assisting with alert triage to enabling predictive insights and automated response—always with human oversight. Each of the five levels above delivers measurable improvements in detection speed, response time, and analyst efficiency, while reducing burnout and operational risk. By aligning AI adoption with SOC maturity and business priorities, organizations can transform the SOC from an overwhelmed response function into a strategic capability that protects what matters most.
Phelix Oluoch
Founder, PhelixCyber
W: PhelixCyber.com